GCP to Azure VPN Connectivity
Today I am going to show how to setup VPN connectivity between GCP and Azure. I have seen this ask from many customers and they want to explore services of other clouds as well. I hope you will enjoy this article the way I enjoyed testing and making it worked.
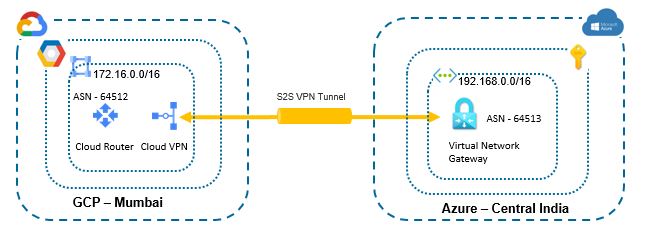
Below is high level VPN architecture between GCP and Azure.
High level architecture
Pre-requisite
- Contributor or Network admin level permission on Azure IAM to create network resources
- Editor or Network admin level permission in GCP IAM to create network resources
- Create Custom subnetwork with 172.16.0.0/24 in GCP
- Create Custom Virtual network 192.168.0.0/16 and subnet with 192.168.0.0/24 in Azure
- Need dedicated subnet for virtual network gateway in Azure
- Public IPs are required for VPN tunnel
High level steps
- Create Cloud Router in GCP
- Create Gateway in GCP
- Create Virtual private Gateway in Azure
- Create Peer VPN Gateway in GCP
- Create VPN tunnel in GCP
- Create Local Network Gateway in Azure
- Create connection in Azure
- Validation from GCP and Azure End
- Test connectivity between GCP and Azure.
Deployment Steps
Create Router in GCP
First step is to create cloud router. It dynamically exchanges routes between your Virtual Private Cloud (VPC) and on-premises networks by using Border Gateway Protocol (BGP).
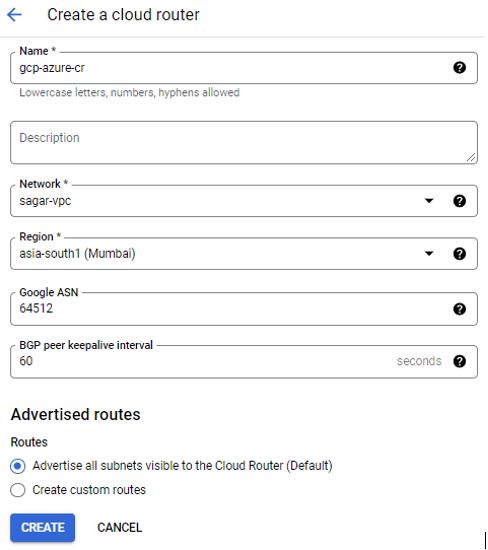
Login into GCP Console, go to network section — > hybrid-connectivity. Click on create Cloud router. Provide name to Router . Name must start with a lowercase letter followed by up to 62 lowercase letters, numbers, or hyphens, and cannot end with a hyphen. Select Network where router applies to . Select Region where you can run your resources.
You need to specify google ASN (Autonomous system number). You can use any private ASN (64512 – 65534) that you are not using elsewhere in your network. BGP-enabled connection between two network gateways requires that their ASNs be different.I have taken 64512 for this demo.
Keep BGP peer keeplive Interval. This is the interval in seconds between BGP keepalive messages that are sent to the peer. If set, this value must be between 20 and 60. The default is 20.
Advertise Routes – Advertise all subnets visible to the Cloud Router (Default)
Create Gateway in GCP
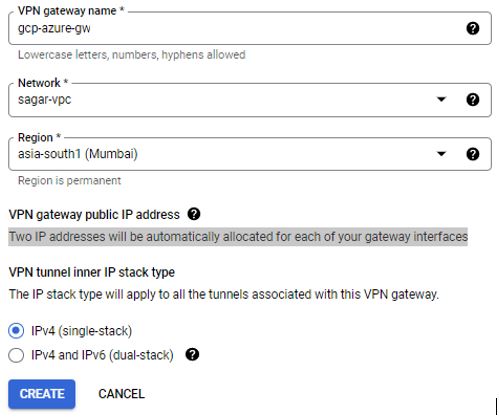
Under Hybrid connectivity, click on VPN. Click on create Gateway. You have two options, Classic or HA-VPN. Classic VPN has been deprecated so we will go with HA-VPN.
High Availability (HA) capable Cloud VPN gateways are regional resources with two interfaces, each interface with its own external IP address. HA VPN connects to an on-premises VPN gateway or another Cloud VPN gateway. In this demo, I am going to setup single tunnel. Provide VPN Gateway Name. Name must start with a lowercase letter followed by up to 62 lowercase letters, numbers, or hyphens, and cannot end with a hyphen. Provide Network to which VPN will connect. Select Region here the gateway to your Compute Engine network is located
Create Virtual Private Gateway in Azure
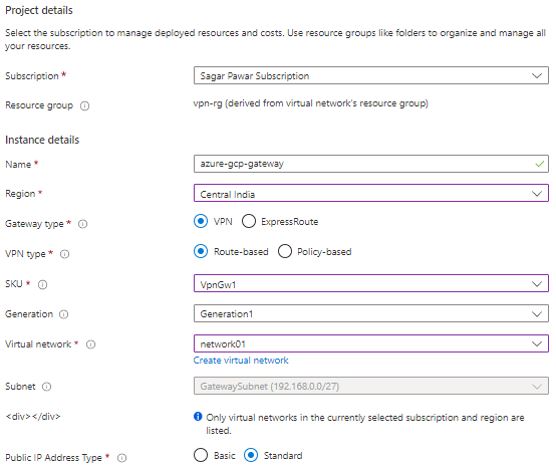
Login into Azure Portal – select existing subscription and resource group, give name to VPN instance , select region. Out of gateway types, select VPN. A VPN gateway is used to send encrypted traffic between your Azure virtual networks or between Azure and your on-premises network.
Out of VPN types, select route based, the type of VPN you can choose depends on the make and model of your VPN device, and the kind of VPN connection you intend to create. Choose a route-based gateway if you intend to use point-to-site, inter-virtual network, or multiple site-to-site connections; if you are creating a VPN type gateway to coexist with an ExpressRoute gateway; or if you need to use IKEv2. Policy-based gateways support only IKEv1
Select SKU, If the current SKU is Basic, Standard, or High performance, it can be upgraded or downgraded to a Basic, Standard, or High performance SKU. If the current SKU is VpnGw1, VpnGw2, or VpnGw3, it can be upgraded or downgraded to VpnGw1, VpnGw2, or VpnGw3. If the gateway is being created to coexist with an ExpressRoute gateway, choose any SKU except for Basic.
Keep Default Generation 1, Generation of VPN gateway, changing Generation or changing SKU across generation is not allowed. Basic and VpnGw1 SKUs are supported on Generation1 only, VpnGw4 and VpnGw5 SKUs are supported on Generation2 only
Select Virtual network, The virtual network that will be able to send and receive traffic through this virtual network gateway. To associate a virtual network with a gateway, it must first contain a valid gateway subnet. A virtual network can’t be associated with more than one gateway.
Gatewaysubnet is auto-detected if already created. If not created , you have to create with min /27 CIDR range.
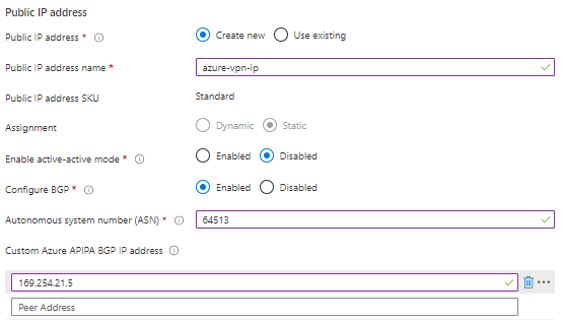
Select Public IP address, provide name, assignment will be static.
If you want HA-VPN , then select active-active mode. In the case, the gateway SKU must be VpnGw1, VpnGw2, VpnGw3, VpnGw1AZ, VpnGw2AZ, VpnGw3Az, or High-performance (legacy SKU).
I need single tunnel, hence I have kept this option disabled
I enabled BGP option. This is available based on SKU size and can be only configured with Route based VPN Gateway with supported SKU type of VpnGw1, VpnGw2, VpnGw3.
Put ASN Number as 64513. Azure virtual network gateways are assigned a default ASN of 65515. Note that a BGP-enabled connection between two network gateways requires that their ASNs be different. If needed, you can change the ASN now or after the gateway has been created.
I have added link-local Private IP, 169.254.21.5. This field is reserved for APIPA (Automatic Private IP Addressing). Azure supports BGP IP in the ranges 169.254.21.* and 169.254.22.*. Review configuration and click on review and create. It usually takes 30-45 to spin-up
Create Peer VPN Gateway in GCP
A peer VPN gateway is the gateway to which this Cloud VPN gateway will connect. It can be an on-premises gateway, a third-party VPN service, or another Cloud VPN gateway. When connecting to another Cloud VPN gateway, you must ensure that the other Cloud VPN gateway is in the same Google Cloud region so that you meet high availability requirements. In our case, we are connecting to Azure Gateway.
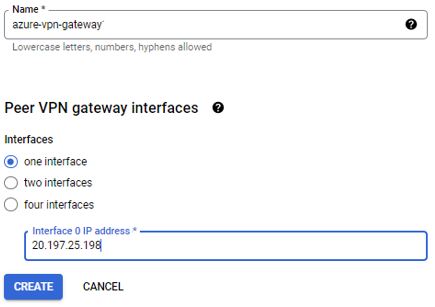
Provide name to peer gateway. Name must start with a lowercase letter followed by up to 62 lowercase letters, numbers, or hyphens, and cannot end with a hyphen
Select interface based on tunnel. At least one IP address needs to be specified. A second IP address of Interface 1 is required when you have a high availability peer VPN gateway with two interfaces. Four interfaces will be needed if you need four tunnels connecting to a Google Cloud VPN gateway of two interfaces. Here I have put public IP address of Azure Virtual Network gateway. Click on Create to provision.
Create VPN tunnel in GCP
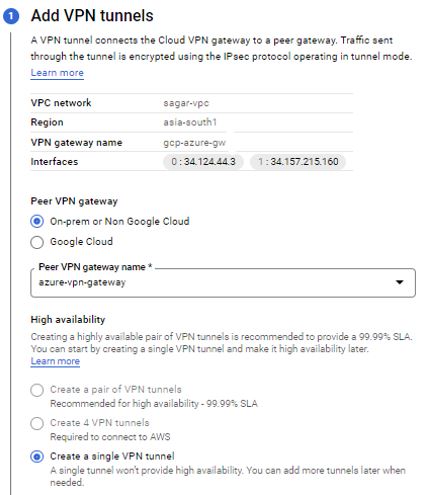
Open GCP console, click on create tunnel. Select gateway created in previous step. The tunnel will be created in the same region as the gateway. This is a high-availability (HA) VPN gateway. You can add single or paired VPN tunnels to the gateway. You can go with a pair of VPN tunnels if you want the high availability and 99.99% uptime SLA. All tunnels created on this gateway must use dynamic routing.
Select on-prem or non google cloud option from peer VPN gateway option. Select cloud router from the drop-down. Interface IPs are auto-generated. Select IKEv2 and generate pre-shared key.
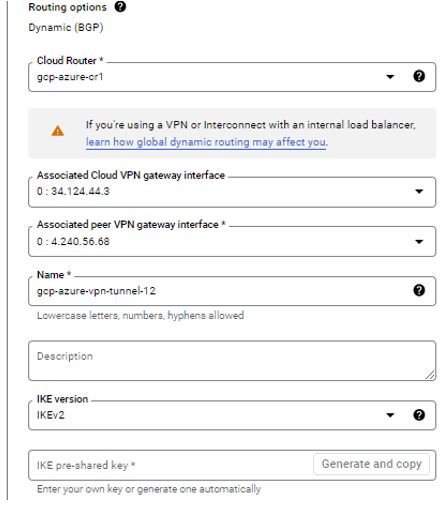
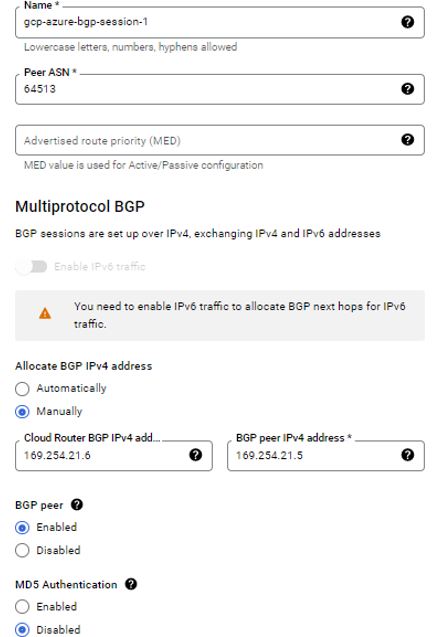
Next Step to configure BGP Session. Provide name to session, Name must start with a lowercase letter followed by up to 62 lowercase letters, numbers, or hyphens, and cannot end with a hyphen. Provide Peer ASN of Azure.
I will keep MED number blank as I am setting one tunnel so no-priority is required. The priority (MED) of routes advertised to this BGP peer. In the case where the peer receives more than one matching advertisement of minimum length, those with lowest priority value win.
Manually I will add link-local IPs. The Google BGP IP and Peer BGP IP must be link-local in the same /30 subnet. Make sure they aren’t the network or broadcast address of the subnet.
BGP peer should be enabled. If enabled, the peer connection can be established with routing information. If disabled, any active session with the peer is terminated and all associated routing information is removed.
I have kept MD5 authentication disabled. MD5 authentication allows you to authenticate BGP sessions between Cloud Router and its peers.
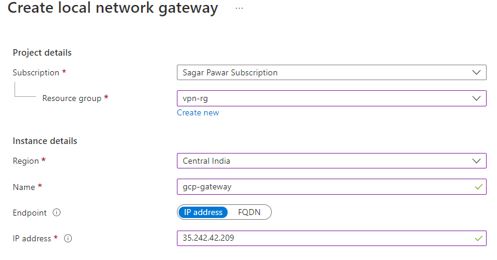
Create local network gateway in Azure
Go to Azure portal, look for local network gateway. Click on create. Select subscription and resource group. Select region. Provide name to local gateway. Endpoint is IP based. Provide Public IP of your tunnel. Under advanced, enable BGP setting, add ASN number set at GCP side and put BGP peer IP address of GCP. This is important step. If it goes wrong, BGB tunnel will not up.
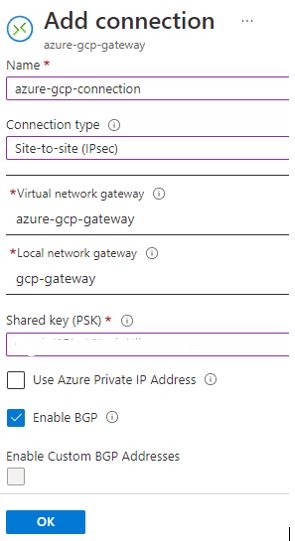
Create connection in Azure
Go to Virtual Network Gateway, Click on add connection. Select site to site connection option. Virtual network gateway is auto-populated. Select local network gateway created in previous step. Add Shared key created while setting up tunnel in GCP. Keep IKE2 protocol as default setting.
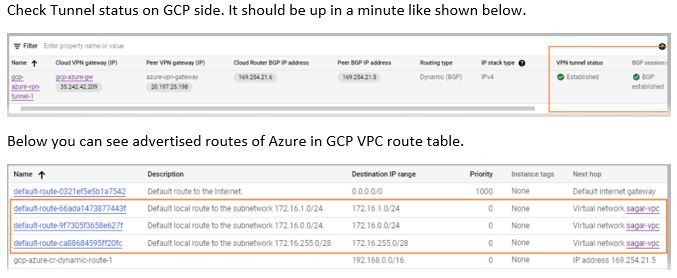
Validation from GCP and Azure End
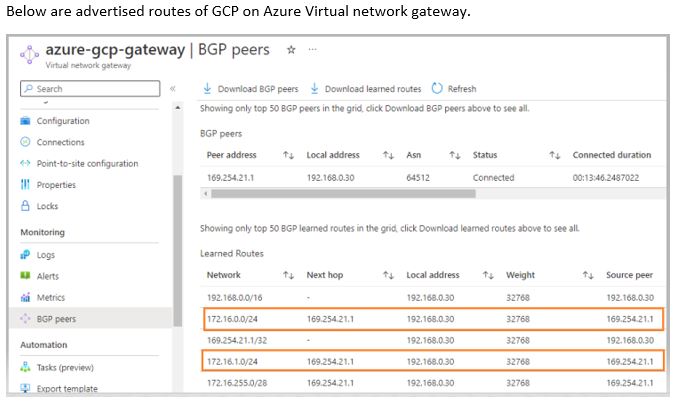
Test connectivity between GCP and Azure
You can create VM in GCP VPC and one in Azure VNET. Update firewall rule on both sides to send traffic. In Source section of firewall rule of GCP, you will put Private range of Azure VPC, 192.168.0.0/16 and same setting you need to do at NSG (Network Security Group) of Azure Subnet to allow GCP VPC, 172.16.0.0/24. Now you can test connectivity between two clouds. It will work smoothly.
You can implement it in your own environment when requirement comes. Thanks for reading. Keep learning with me.
3 Comments