Security Team always prefer Azure Private Link service for better security
Today we will understand what is private link and how to use it. Azure Private Link enables you to access Azure PaaS Services and Azure hosted customer-owned applications over a private endpoint in your virtual network. Traffic between your virtual network and the service travels the Microsoft backbone network. Communication is one way. At time, you can become Consumer or provider. If you are consumer, then you will create private endpoint to connect. If you are provider, then you will create private link service.
Today I am going to cover how to setup private link for Consumer and Provider. I will show you how you can access Azure service within cloud and from on-premise. I have divided this article in three parts
- Accessing Private Endpoint within cloud
- Accessing Private Endpoint from on-premise System
- Setting up azure private link with third party
A. Accessing Private Endpoint within cloud
I already have Storage account with public endpoint. I am going to configure private endpoint. You can configure it during storage account creation or afterwards as well. You can create from networking section of managed service or private link service option.
Login into Azure Portal, open storage account service, go to network section and private endpoint connection. Click on create a private endpoint, provide subscription and resource group details. Provide name, Network interface name is auto-populated based on name. You can change it if you want. select region. Make sure Private link and your Virtual network should be in same region. On next screen, select blob as resource. It is always recommended to have separate subnet for private endpoint and add available services that support private endpoint. Under networking section, your network and subnet is auto-populated. You can allow to allocate IP dynamically or assign it manually. Proceeding further, do private DNS integration. select subscription and resource group where you want to create or add records in private DNS zone. Review and create it.
Below is option from where you create private endpoint for PaaS Services.
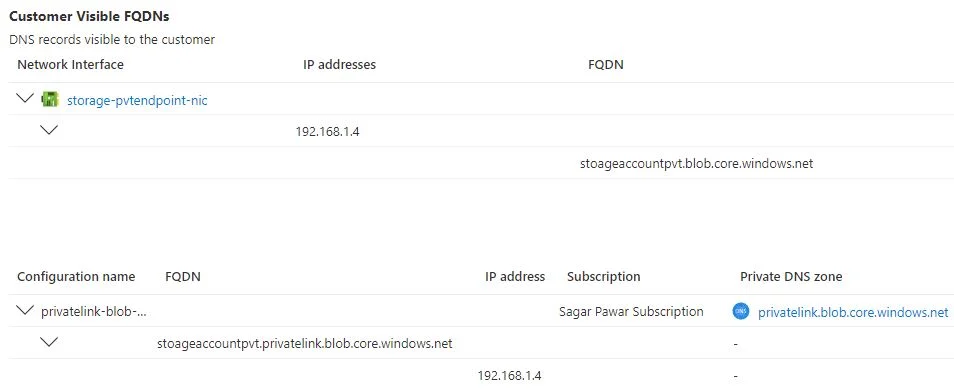
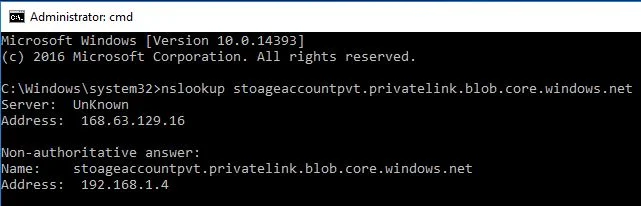
After creation, you will see below endpoint details. If you resolve the FQDN from any VM in that network or peering with that network, you will get private IP of PaaS service. The IP #168.63.129.16 is global DNS server of Microsoft. If you do not set any custom DNS server, all VMs in Azure Cloud, takes this default DNS server for resolution.
B. Accessing Private Endpoint from on-premise System
In case there is a requirement to access Private endpoint from on-premise system. Couple of things to note down. First thing is to check hybrid network connectivity. In this connectivity, your Virtual private gateway sit in hub network and it gets peered with spoke network. If your private endpoint has taken IP from spoke network, then it should be peered first.
On your on-premise system, you use local DNS server. First thing is to place one windows machine with DNS role installed. This server will point to Azure Global DNS server to forward DNS query coming from on-premise Network. It works as DNS forwarder. Your local DNS server should have conditional forwarder to forward Private link request to Windows DNS server in Cloud.
Azure Private link DNS flow
- Client PC initiate DNS query to access Azure PaaS service on Private link FQDN.
- Request will go to local DNS server having conditional forwarder towards Cloud DNS forwarder
- It will forward the request to Azure Global DNS server
- As Azure Global DNS server has info about private cloud DNS zone, it will contact private DNS zone, get A record against Private link FQDN
- Cloud DNS forwarder get A record from Azure Global DNS server.
- it will give query response to local DNS server
- Local DNS server give it back to Client PC
- Client PC access Azure PaaS service on private IP assigned to it.
Below is Private link DNS flow architecture

C. Setting up private link with third party
Let’s understand architecture to start private link service
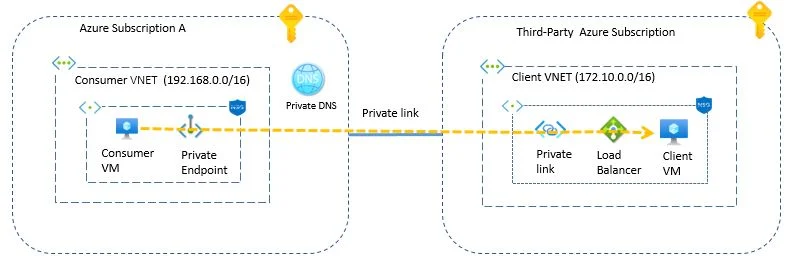
In the above diagram, you will see that Consumer VM want to access service on client VM. Both have different network range. VPC peering or VPN option are available but it is not recommended to expose our network with third party hence I am going with private link service as it is much secure as i am exposing only port 80 to connect to remote system.
High-level steps
- Get editor or network admin access
- Create internal load balancer in third party subscription
- Create Private link service in third party subscription
- Create Private endpoint in Consumer subnet
- Create private zone and add A record for private endpoint — Optional
- Testing
Deployment steps
Internal Load balancer
Login into Third party Azure portal. Connect with subscription. Open load balancer console. Create load balancer.
Select subscription and resource group. Provide name, select region. select standard SKU. As this is internal Load, select type Internal and tier Regional.
Do frontend configuration. Give name, select static or dynamic assignment, select network and subnet from where IP will be allocated
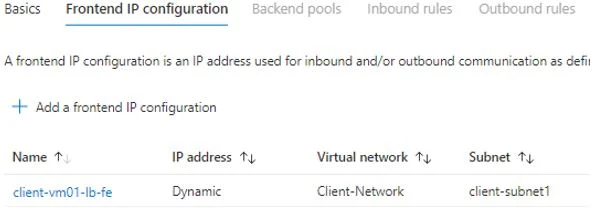
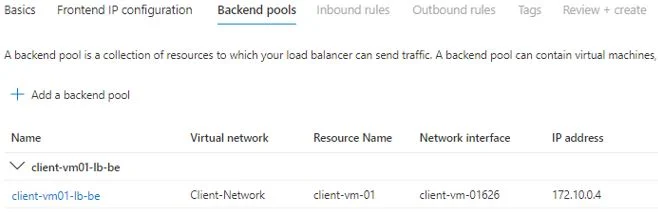
Next thing is to set backend pool where you will specify the backend node which will receive a traffic.
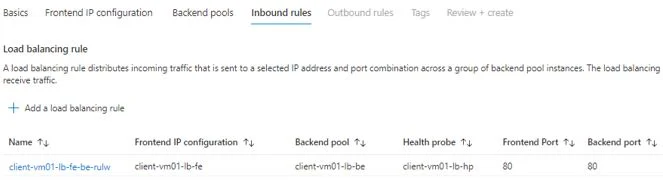
Setting inbound rule is important step. You will enable connection between frontend and backend. You will specify on which port traffic will receive and on which port traffic will be redirected to backend node. You will also specify health check to monitor backend node status. Review and Create LB.
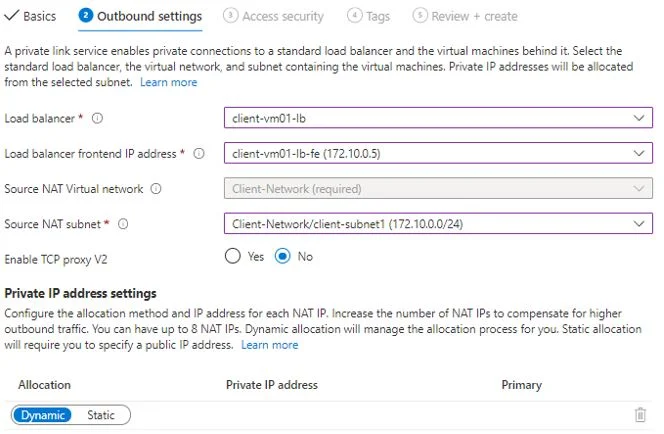
Private link service
On basic page, select subscription, resource group. Give name and select region.
In outbound setting, specify Load balancer, Load balancer frontend IP is auto-populated. Source NAT virtual network is same as Load balancer network. You can either use existing subnet for Natting or create new range from same network. IP allocation you can keep static or dynamic.
Under access security, determine how your private link service will be consumed by consumers without existing permissions. You can expose it using a short friendly name, and auto-approve connections from trusted subscribers. If you already have permissions to the subscription that hosts this private link service, no action is required on this page.
The visibility of private link service setting determines who can request access to your private link service.You can select either of them. I have selected Role based access for more restriction.
- Role-based access control only: This private link service will only be available to individuals with role-based access control permissions within your directory. (Most restrictive)
- Restricted by subscription: Any user with access to specific subscriptions (that you’ll add below) can request access to your service, even across directories.
- Anyone with your alias: Anyone with your private link service alias can request access to your service. (Least restrictive)
Private endpoint
On basic page, select subscription, resource group. Give name and select region. Network interface is auto-populated. You can modify if you want.
Under Resource page, provide Private link resource id or alias. You will get it from Private link service overview page

Select virtual network and subnet from consumer VNET. You can specify dynamic or static IP allocation
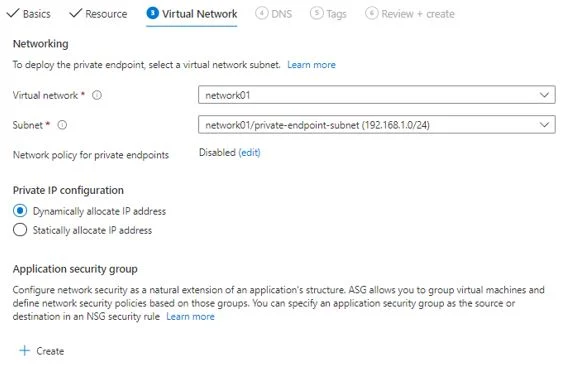
Private DNS integration will be disabled if you have not created any private DNS zone. This step is optional. if you want access provider service on private DNS then you need to enable it. This step will create A record pointing to Private IP of endpoint in Azure Private DNS zone. You can perform this step later as well. You can also utilize your own DNS server or create DNS records in host file of consumer VM.
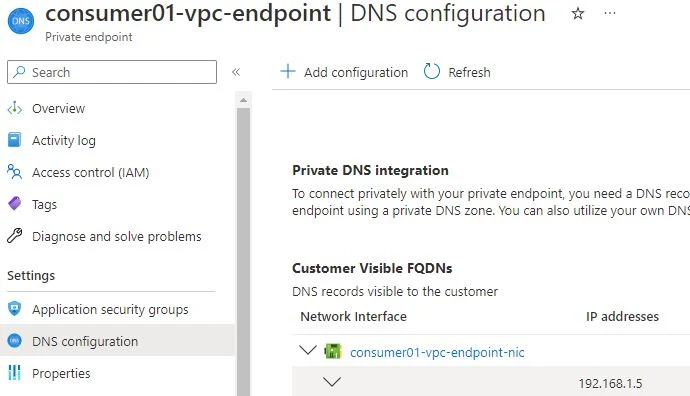
Review all steps and create it. Check private IP allocated to endpoint.
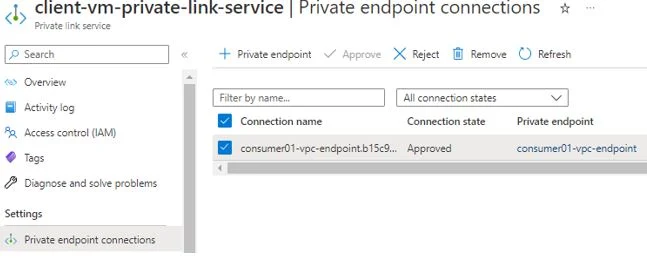
Next point is to approve endpoint connection from private link console.
Final step is to do testing. I am accessing the Client Server from private endpoint created in consumer network.

Azure Private Link can integrate with Azure Monitor. You can monitor Data processed by the Private Endpoint (IN/OUT) and Private Link service (IN/OUT)
I have explained all Azure Private link service in detail. You can implement the same in your orgnization. Reach to me if you have any question. I will be happy to help.
3 Comments