Improve Azure PaaS Services Security with Native Connectivity
If you take any Azure PaaS service. It comes with a public endpoint so it is very critical for organizations to restrict access while leveraging such a service.
As a cloud architect or security engineer, you have to make a secure connection to PaaS based service. This is very critical from a design perspective. Today we will see what options we have in this regard.
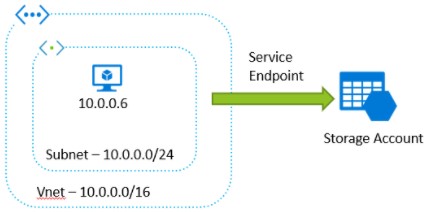
While securing access to a public endpoint, the service endpoint comes in handy. It is part of your virtual network which provides secure and direct connectivity to Azure services over an optimized route over the Azure backbone network. Service endpoints enable private IP addresses in the Virtual Network (VNet) to reach the endpoint of an Azure service without needing a public IP address on the VNet.
Below is the diagram that depicts that VM with private running inside virtual network and want to access storage account. To achieve this, first enable the service endpoint to the only virtual network where VM is running.
Steps To Enable Service Endpoint
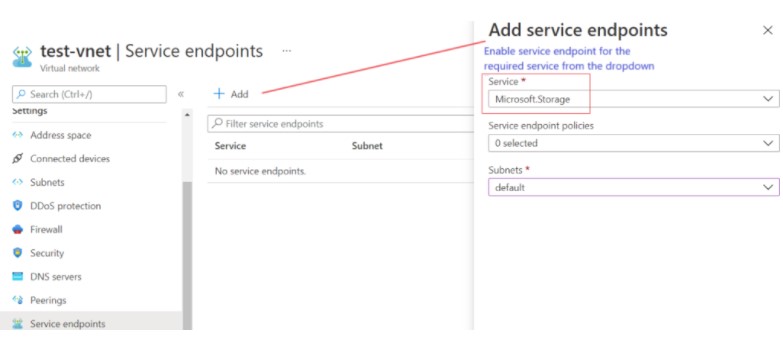
Step 1: Enable service endpoint on the required Virtual network. Endpoint policies can be optional. It allows you to filter virtual network traffic to Azure services.
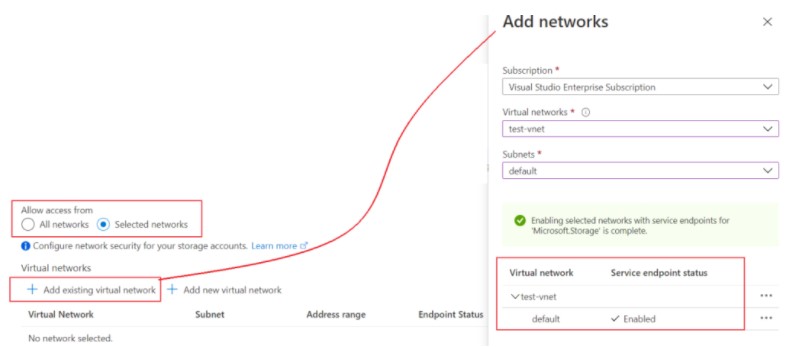
Step 2: Go to the firewall or network setting of the PaaS service and add the service endpoint.
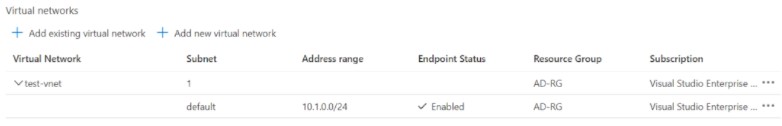
Step 3: Verify the endpoint service is enabled to use.
Important Points to Note for the Service endpoint
- Ensure IP firewall rules are allowed before setting up service endpoints.
- The service endpoint does not support on-premise resources to connect to PaaS-based service. You have to use either on-premise NAT IP or express route in that case. You must allow these public IP addresses in the resource IP firewall setting.
- The service endpoint is limited to a few PaaS-based services. The available Services are Azure Storage, Azure Database services, Azure Synapse Analytics, Azure Key Vault, Azure Service Bus, Azure Event Hubs, Azure Data Lake Store Gen 1, Azure App Service, and Azure Cognitive Services.
- To access SQL and Data lake service over service endpoint, VNet and PaaS services should be in the same region.
- The service endpoint does not resolve DNS queries
You do not need to pay additional charges for service endpoints and there is no limit on the total number of service endpoints to create.
====================================================================
After discussing the service endpoint, now we will see about the Private endpoint. It uses a private IP address from your Virtual network (VNet), effectively bringing the PaaS-based service into your Virtual network. It is a network interface that connects you privately and securely to a service powered by Azure Private Link.
Below is the diagram that depicts that VM with private running inside virtual network and want to access storage account. To achieve this, first set up a private endpoint to only the virtual network where VM is running.
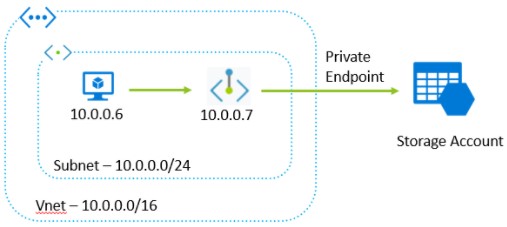
Steps to Configure Private Endpoint
Step 1: Go inside the PaaS service, the private endpoint creation option will be available inside the firewall and networking section or a separate section will be given.
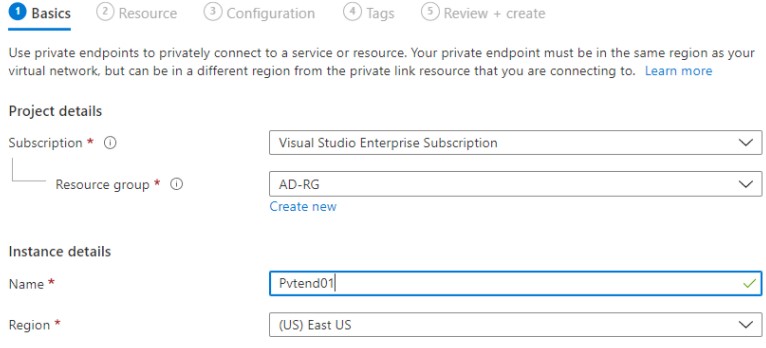
Step 2: Private Link offers options to create private endpoints for different Azure resources, like your private link service, a SQL server, or an Azure storage account. Select which resource you would like to connect to using this private endpoint.
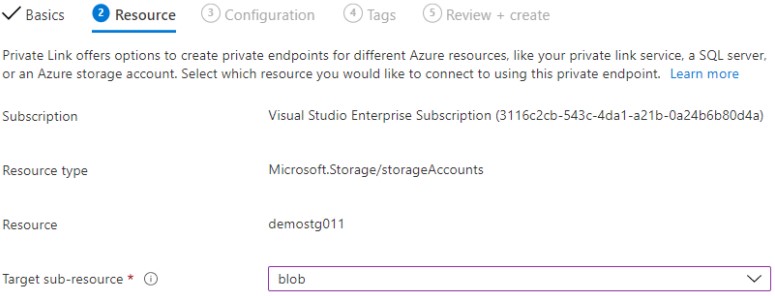
Step 3: Here you have to choose a virtual network/subnet and do private DNS integration. To connect privately with your private endpoint, you need a DNS record. Once this is configured, you can create the service.
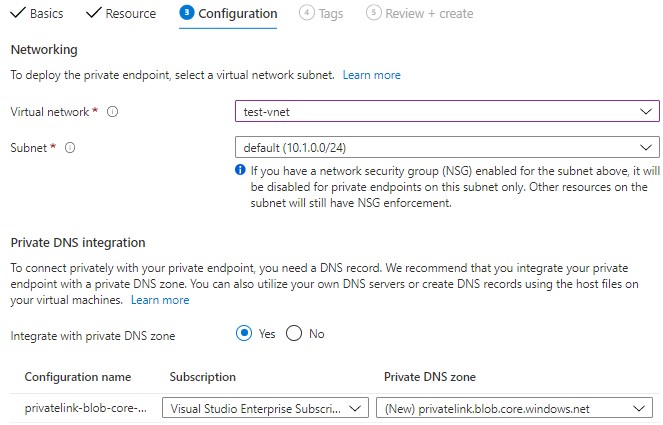
Step 4: Verify the Private endpoint service is created and is operational. It is visible under the virtual network section as well as under the service -> Networking section
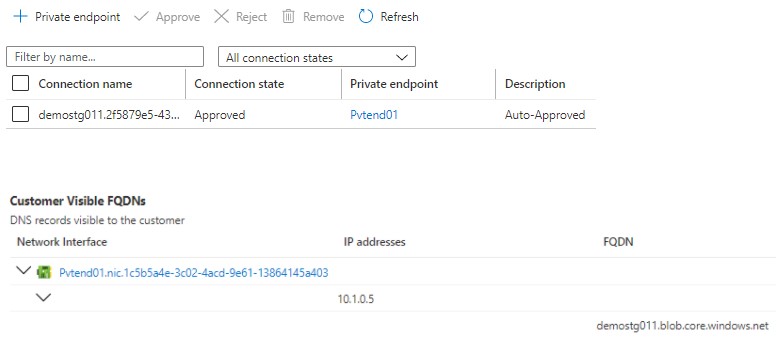
In our case private link connection is auto-approved as we have RBAC permission, if it is not then, it goes for approval to the consumer. They have access to approve or reject the connection. There are four connection statuses of the Private endpoint you can notice. They are Approved (auto or manual approval is provided), Pending (approval is not received), Rejected (not approved ), Disconnected (connection removed).
To deploy a private endpoint or private link service, a user must have assigned a built-in role like Owner, Contributor, or Network contributor.
Also, we have created a private endpoint only for the blob of the storage account. If you need secure access to other resources of storage accounts, like files, tables, or queues then you need to have a separate private endpoint connection in place.
Private endpoint supports a wide range of Azure services and it is not limited to the public cloud. It supports a hybrid cloud as well. My on-premise VM can connect to Azure services powered by a private link over VPN or express route.
With every private endpoint, one NIC is created with dynamic private IP of the same subnet. The value of the private IP address remains unchanged for the entire lifecycle of the private endpoint.
Every service comes with some limitations as well. Here are those:
- Support only IPv4 traffic.
- Work on TCP and UDP traffic.
- Basic Azure LB is not supported.
The Azure security center having Azure security benchmark provides recommendations on how you can secure your cloud solutions on Azure.
Unlike Azure service endpoint, private endpoint comes with charges for endpoint creation, ingress/egress data processed.
On a closing note, I would suggest choosing the service endpoint and private endpoint wisely. A service endpoint remains a publicly routable IP address. A private endpoint is a private IP in the address space of the virtual network where the private endpoint is configured.
Leave a Reply