AWS Organization to manage multiple AWS Accounts through a single console
Before AWS organization, account creation has been doing manually. For Enterprise organizations, multiple account creation for multiple domains/platforms/business units was time-consuming.
AWS organization service solves this problem by creating an AWS account programmatically. It is a central management service that allows you to control all resources that come under different accounts and give consolidated billing of all accounts. It does policy-based and group-based account management. AWS Organizations is integrated with other AWS services so you can define central configurations, security mechanisms, and resource sharing across accounts in your organization.
IAM policies enable you to allow or deny access to AWS services for users, groups and roles whereas Service Control policies enable you to allow or deny access to AWS services for individuals or group accounts in OU. Hence it is recommended to choose SCP (Service Control Policies) wisely which creates permission boundaries. You can attach a policy to the entire organization, to OUs, or directly to an individual account. You can apply SCPs to only member accounts in an organization. They have no effect on users or roles in the management account.
High-level steps are, Setting up a root organization with a default account, creating organization units (OU) with a management account, creating policies and Enabling AWS services that support AWS Organizations.
You can access organizations by management console, command line tools, SDKs and Rest API.
It creates root organization for your AWS account. Under Root, you can create OU which is nothing but a logical grouping of your multiple accounts. Under OU you can create multiple nested OUs. It is best practice to create OU based on functions rather than company structure.
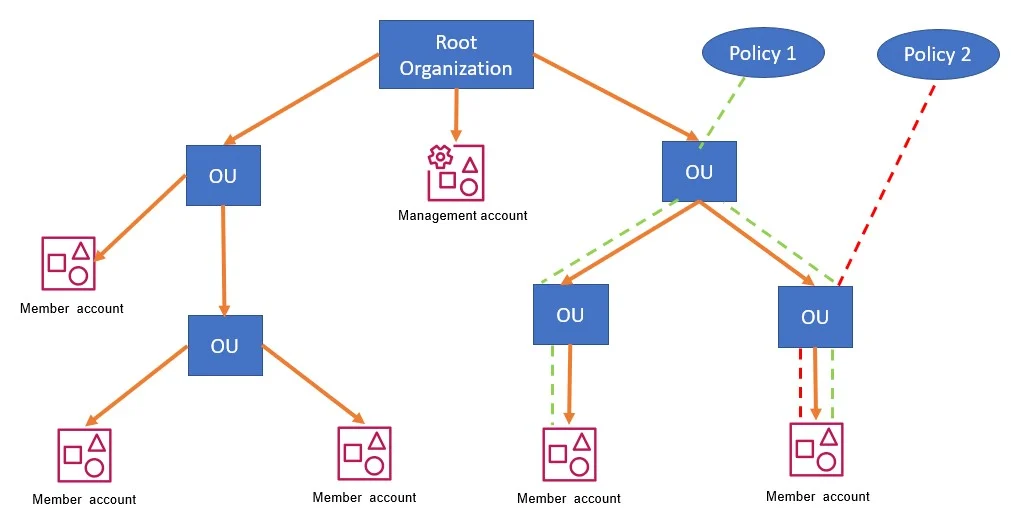
When you create a new AWS account or invite AWS accounts from the organization console, it goes into root org by default, you have to move it to the correct OU.
Invited accounts become members when they accept the invitation by replying to an email or by calling the AcceptHandshake API. Member accounts are administered and managed by the organization.
I have created the below OU structure to show you.
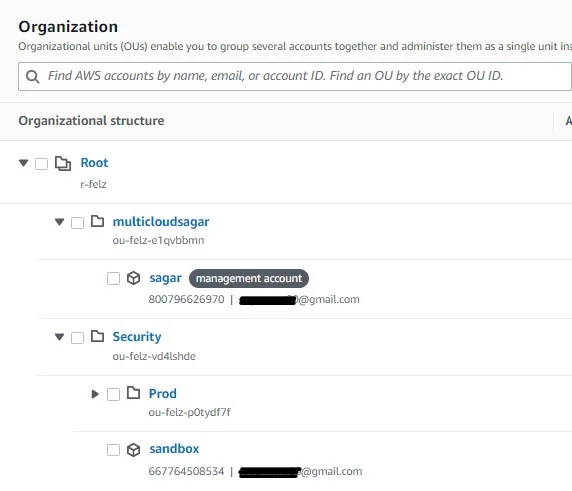
Commom use cases could be,
- Automate the creation of AWS accounts and categorize workloads
- Define and enforce audit and compliance policies
- Provide tools and access for your Security teams while encouraging development
- share central resources within the organization
Under policies, you get four policy types initially, which you can enable based on your requirements
- AI services opt-out policies
- Backup policies
- Service control policies
- Tag policies
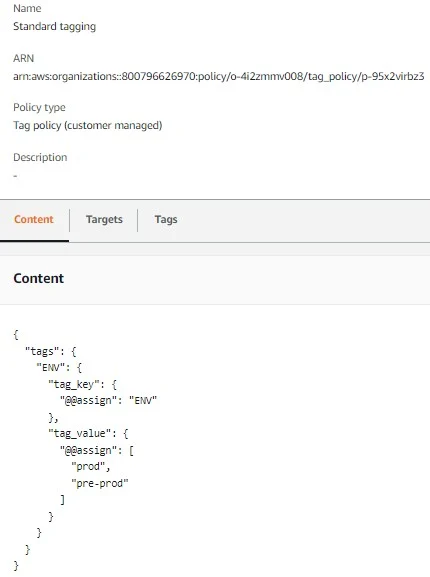
I will talk about Tag and SCP policies. First go to the policy section and enable tag policy. Click on create policy. I have created one policy under it that will apply ENV key to all resources with Prod and pre-prod values to choose from. The policy target is my management account as of now. It looks like the one below.
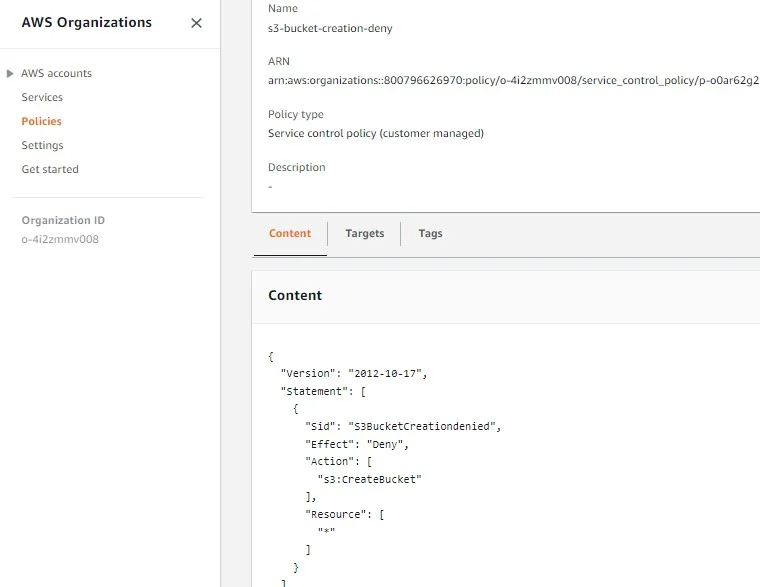
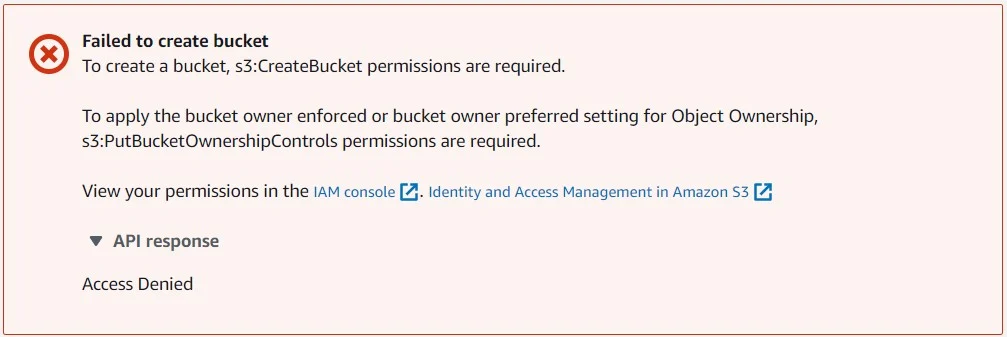
Similarly, I have added an SCP policy to deny S3 bucket creation. Attached to my sandbox account.
When I login into my Sandbox account, and try to create S3 bucket, I get the below error. It means it is denied by central policy. This is how you can create and apply policies.
AWS organization is available for all without any additional charge.
I hope This article has given you an idea of what AWS Organization is all about and how to configure it.
Leave a Reply