5 ways to connect GCP services on the private endpoint
When you access any cloud services, the expectation is to do it securely. There is no difference when you work on the Google Cloud Platform. Google has to comply with the security standards of any organization.
Even Google cloud services are away from customers but they should be accessible on private IP rather than using public IP. To meet this requirement, Google Cloud provides several private access options that let virtual machine (VM) instances in Virtual Private Cloud (VPC) networks reach supported APIs and services without requiring an external IP address.
The five types of private access include private service connect, private Google access, private Google access for on-prem hosts, private service access, and serverless VPC Access
1. Private Service Connect allows private consumption of services across VPC networks that belong to different teams, projects, or organizations. You can keep your application running behind a load balancer and then publish that service for customers by providing access to their project. The customer has to create an endpoint to connect these published services smoothly. Every endpoint creates its own DNS records in the Cloud DNS service. Please note this works in the uni-directional mode so there are always requests initiated from the consumer end.
Private service Connect can extend to on-premise resources as well. If the consumer is in the GCP cloud then they can connect to published services via an endpoint, that forwards the request to the load balancer and it uses NEG (Network endpoint Group) at the backend to reach on-premise servers. The only limitation is that if the consumer IP belongs to an on-premise network, then it will not work on the direct-interconnect link as of now. You only need to provide a VPN tunnel.
Whenever we use a load balancer then health checks come along with it. To monitor health checks of systems, you need to create an ingress rule to allow two public ranges (35.191.0.0/16,130.211.0.0/22) of GCP otherwise health check fails.
You can use Private Service Connect to access Google APIs and PaaS services, or managed services in another VPC network.
2. Private Google access clients consist of Google cloud VM instances does not require public IP to access GCP APIs and PaaS services. Only the Assigned private IP of the VM, can be able to connect to APIs and PaaS services.
You need to enable Private Google access on the subnet level not on the VPC level, If your VM is running into a subnet for which private google access is enabled then only VM can access PaaS Service without public IP. Enabling Private Google access on a subnet as shown below.
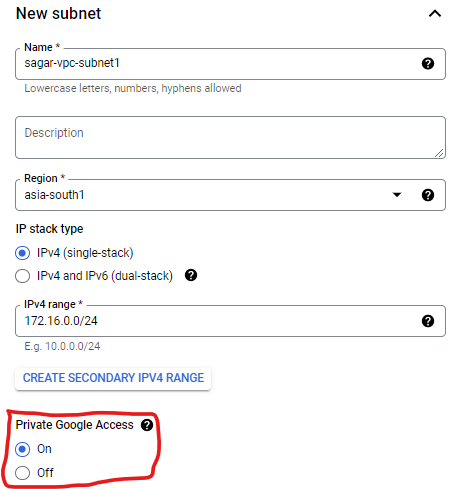
In case private access is not enabled on your subnet, then also you can access APIs and PaaS services via public IP.
3. Private Google access for on-prem hosts – when the on-prem system wants to connect with Google APIs, IaaS and PaaS services then you do not need to enable Private Google Access on the subnet. You have to either set up Cloud interconnect or Cloud VPN. This is also called hybrid connectivity.
To set up hybrid connectivity, you need at least a network admin role. It supports only IPv4 addresses. The cloud router service is used to configure VPN or Direct interconnect. The on-premise network must have appropriate routes for either the private.googleapis.com or restricted.googleapis.com destination IP ranges.
consist of on-prem servers which want to connect to google APIs and services through VPC Network on private IP. To access the service privately, a VPN tunnel or cloud interconnect is required.
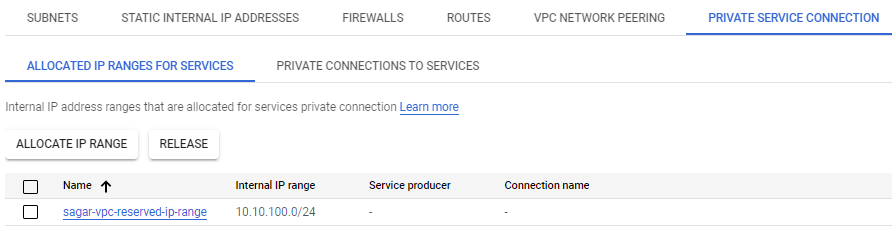
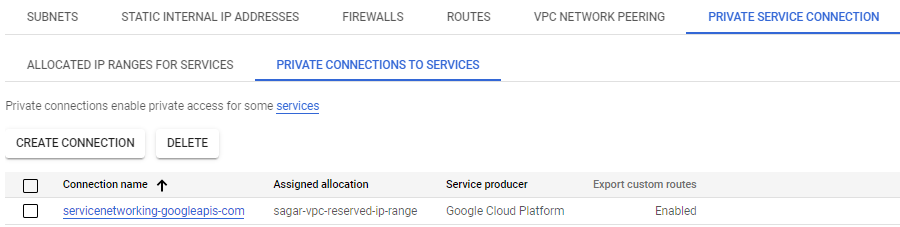
4. Private service Access is nothing but a private endpoint that can be used for Google and third-party services with internal IP addresses that are hosted in a VPC network. Private services access requires first reserving an internal IPv4 address range for creating a private connection for managed services.
For example, if you want to access Cloud SQL service on private IP then you will reserve a private IP range. next thing you will create a private connection. This connection allows VM instances in your VPC network to use internal addresses to reach Cloud SQL service.
5. Serverless VPC Access, as the name suggests, is designed for serverless services such as Cloud Run, App Engine, or Cloud Functions and makes them accessible on private IPs for cloud VM instances that do not have external IP addresses.
same as private service access, you have to reserve /28 range when using the connector to connect serverless environment. The connector can be created as shown below.
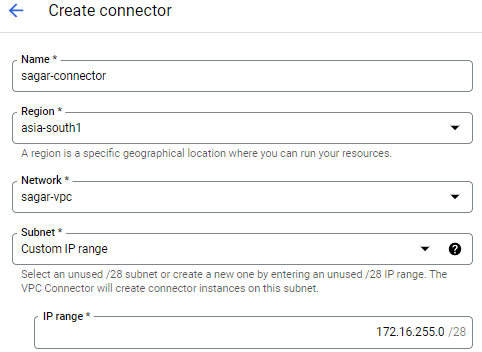
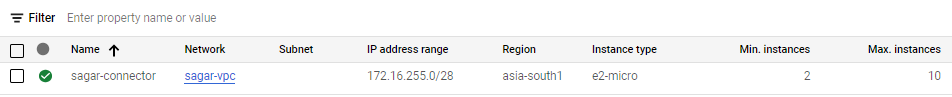
Along with a bunch of firewall rules get added
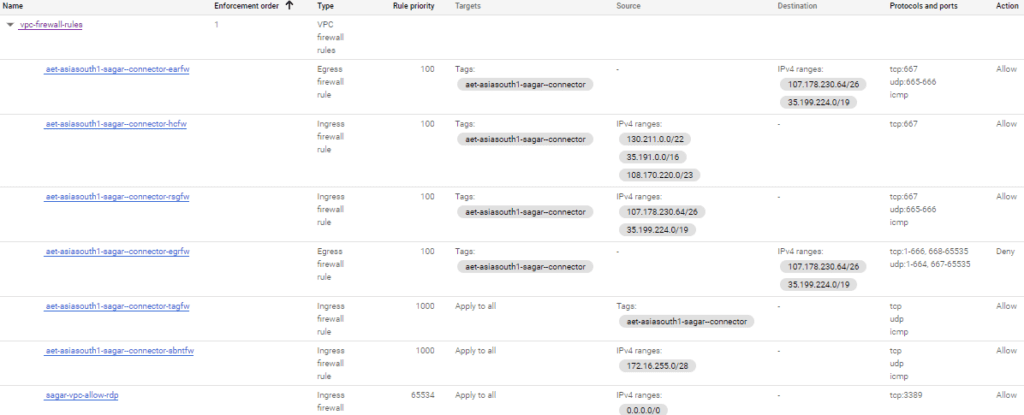
Serverless VPC Access allows Cloud Functions, Cloud Run (fully managed) services, and App Engine standard environment apps to access resources in a VPC network using those resources’ private IPs. The connector handles sending and receiving both the requests and responses directly from these internal IP address
I hope this article has helped you to understand which private service of Google to be used when. Happy Learning.
Leave a Reply