Connect GCP VM from anywhere without public IP or VPN
If your VM do not have public IP or do not have hybrid connectivity via VPN, you can use Identity Aware Proxy (IAP) which is unique feature of GCP cloud at this moment. It does TCP forwarding which allow you to establish an encrypted tunnel between your home or office N/W and Google datacenter where your VMs are hosted. Good point here is that you do not need to setup hybrid connectivity so setup and bandwidth cost will be saved. You only need home internet and valid credential provided to connect and leave rest of things on Google to take care for you.
Through IAP, you can access to services hosted on App Engine, Compute Engine, and an HTTPS Load Balancer. You can extend secure connection to on-premise App by using IAP Connector. Today we are going to see how to connect VM created in GCP Compute Engine.
Identity Aware Proxy Architecture Diagram
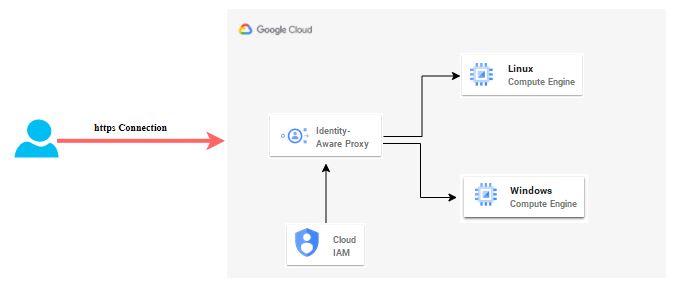
Pre-requisite to on-board Identity Aware Proxy
- Need owner permission on GCP console
- Create Subnet network
- Create a Windows and set the credential
- Create Linux VM and set SSH key
High level Steps
- Open firewall rule for GCP
- Provide IAP Permission
- Validate IAP Configuration
- Setup IAP Desktop tool
- RDP and SSH testing via IAP
Deployment Steps
- Login into GCP Console with administrator permission. Open VPC network — > Firewall. You have to add a GCP CIDR range, 35.235.240.0/20 as source and Destination would be your VMs with specific tags like IAP Allow or all instances in network. IAP will use this range for TCP forwarding on Windows and Linux VMs on port 3389 and 22 respectively.
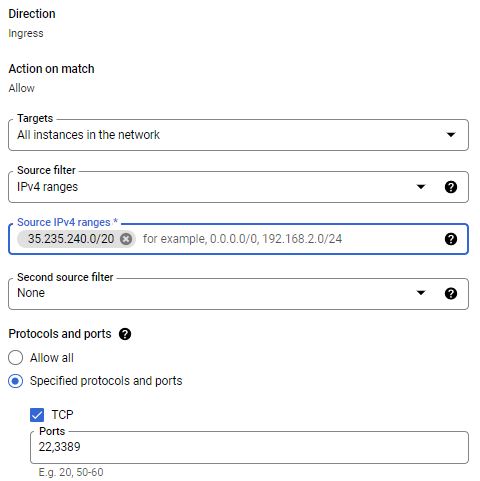
2. If you are going to manage IAP in your project, need IAP Policy Admin access. Provide IAP-secured IAP-secured Tunnel user to Users who are going to access VM via IAP tool. If user already has owner permission, no additional permission is required to manage or access it.
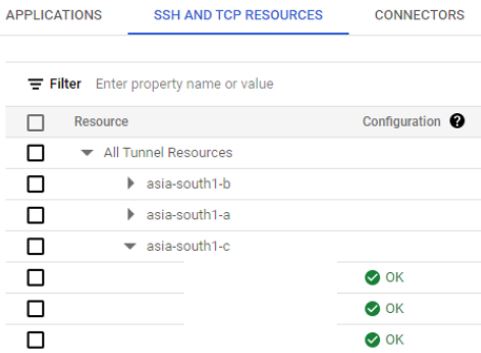
3. In GCP console, search for identity-aware Proxy feature. Go to SSH and TCP resources and check Identity aware proxy setting on your VMs. Configuration status should be OK. If it is in warning state, you will get option to enable it.
4. Now you are set to do testing. You can do this test via gcloud and IAP desktop tools. I will show you simple method to access your GCP VMs via IAP desktop. Download IAM Desktop from the link – https://github.com/GoogleCloudPlatform/iap-desktop/releases/latest/download/IapDesktop.msi. Click on it to install. It takes less than 30 sec to install on your device. When launch it, will ask you to login with GCP console credential. You need to allow IAP Desktop to update your google data. This is important step to understand before proceeding. IAP Desktop requires it to access your Google Cloud projects, and do IAP TCP forwarding.
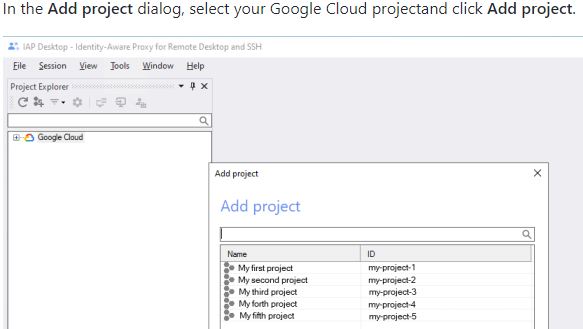
Once it finish, IAP desktop will ask you to select required project from drop-down. It will list all VMs under it. It will also show which VMs are running.
To connect to windows VM, click on VM, it will ask to enter local login credential if set already. It will also give you option to generate new windows credential. If you want avoid this step, set your local credential in connection setting of that VM. Next time onwards, it will login automatically.
To connect SSH VM. Click on VM. Put your SSH key and connect. Here you also have option to set SSH key so you do not need to enter again.
You can also launch IAP Desktop from within a web browser by using iap-rdp:///project-id/zone-id/instance-name. Initially you have to open IAP Desktop and enable browser integration option from Tools — > Option.
IAP automatically disconnects sessions after 1 hour of inactivity. Enable Cloud Audit Logs for your Identity-Aware Proxy (IAP). Cloud Audit Logs lets you view a request and see all the access levels. You can use a group policy object (GPO) to automatically install IAP Desktop.
Many customers have been using this option as it is easy to go option. IAP save lot of your time to setup secure tunnel and manage it.
Leave a Reply