Multi-Cloud Server Management with Azure Arc Service
Azure Arc is a service or an offering in Microsoft Azure that provides a centralized management of all the resources that exists in on-premise and multi-cloud environments. It is specifically designed to on-board non-azure resources to Azure. The Non-azure resources will become Azure resource after on-boarding.
What will you do with this service? When you create azure resource on Azure portal, you can install log analytics agent, enable Microsoft defender for cloud, Sentinel and azure policy through Azure portal. You can do automation through templates and extensions. All these things are possible with non-azure resources. You can also do inventory management of resource through it. Overall you can govern, protect, configure and monitor resources.
Below diagram depicts what we discussed. It gives overall view of the service capability.
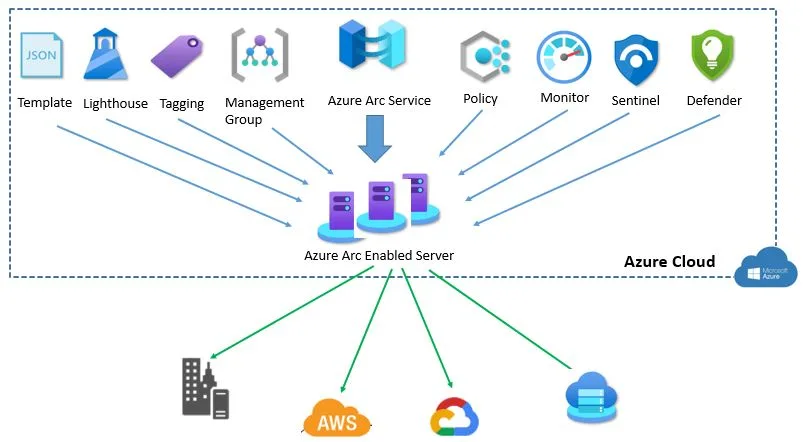
Azure Arc is free service but when you use Azure services like Cloud defender for Microsoft or any other Azure management services shown in above diagram, you have to pay charges for using it based on rate card.
Once non-azure machine gets connected, it stores metadata information about it and stored in the regions where Azure Arc machine resource is selected. The Connected Machine agent sends a regular heartbeat message to the service every five minutes.
Azure Arc enabled servers support VMware, AWS, GCP and Azure Stack HCI.
Below are best practices for on-boarding Server to Azure ARC
- Verify supported operating system for arc enabled servers.
- Create separate resource group to on-board azure arc resources
- Assign Arc specific RBAC role at subscription or resource group level
- Apply tags to all resources
- Arc service enable Azure region should be geographically closest to non azure machine location
- Define what all services you are going to access
- Keep dedicated log analytics workspace if you are using log analytics agent
- On-board policy to check for compliance
Pre-requisite to use Azure Arc Service:
- All Arc enabled server should allow to connect Microsoft URLs on Port 443.
- Administrator permission to install agent and do configuration
- Decide on how Arc enabled servers connect to Azure , via internet through proxy or Private endpoint
- Create service principle account with “Azure Connected Machine Onboarding” RBAC role
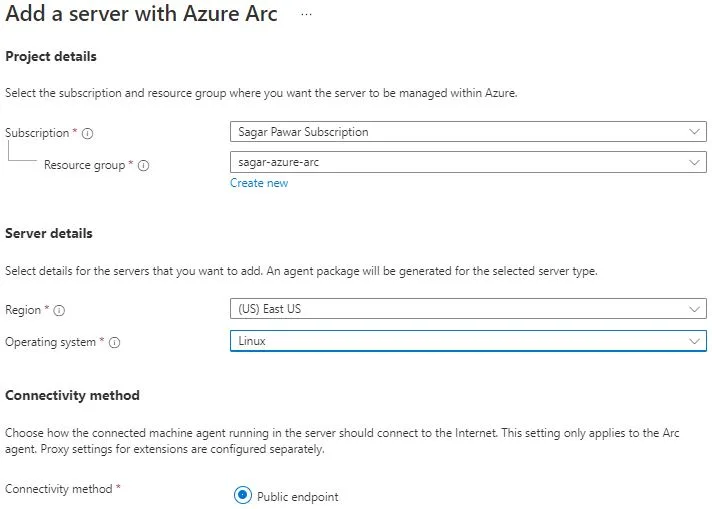
You do not need to create Azure Arc Service. You can login into Azure Portal, search for azure Arc service, on left side of pan, you click on servers option. Add non-azure servers. Either I can choose single server or multiple servers. For Demo, I will go with single server to begin with.
On Single server option, you can generate script. Before that, you need to provide basic info.
like subscription name, resource group, region, operating system and connectivity method. You can use defined tags or create custom tags. Download the script to execute on non-azure servers. In my case, I will use one AWS and one GCP VM for testing.
This script does:
- Download the agent from the Microsoft Download Center.
- Install the agent on the server.
- Create the Azure Arc-enabled server resource and associate it with the agent.
For Script execution in windows machine, you need to open PowerShell with admin privilege. You either copy and paste content of script or download script in that machine. During execution, it will prompt Azure portal URL login to authenticate credential. You will notice “Azure Hybrid Instance Metadata Service” is running in windows machine.
For script execution in Linux machine, you need to copy the script. Provide sudo permission to user and Make the script executable with command chmod +x.
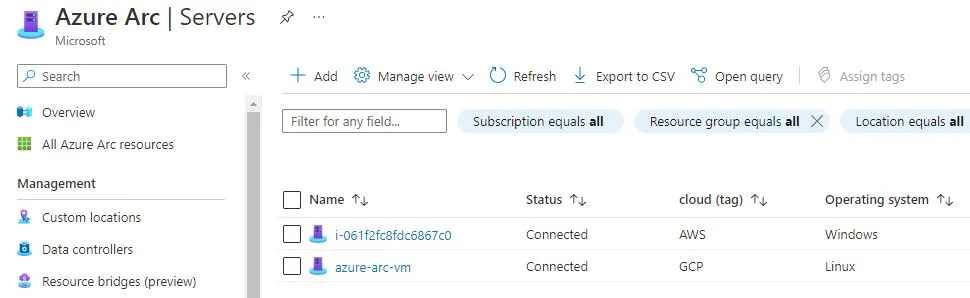
After doing above steps, you will find AWS and GCP VMs are onboarded.
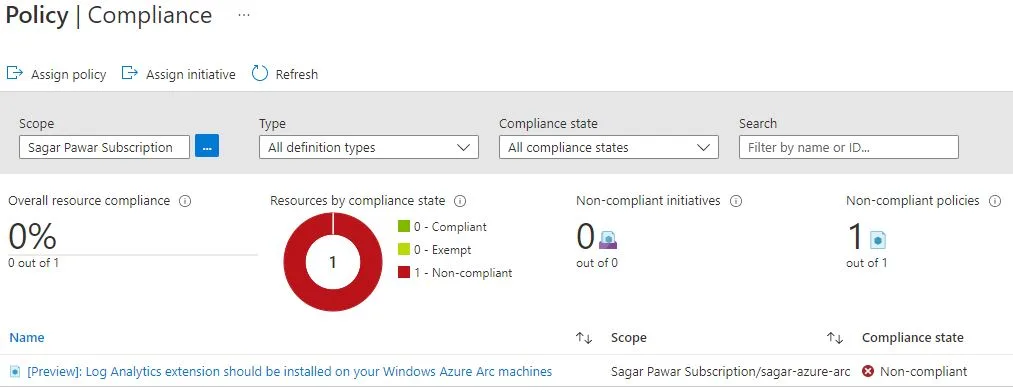
Next step to apply policy. Launch Azure policy service in the portal. Click on Assignment on left side pane. Click on assign policy, select scope. in our case, I have selected sagar-arc-rg group. I have selected the policy definition Log Analytics extension should be installed on your Windows Azure Arc. I have got a result as non-compliant as I did not install log analytics agent.
Next we will see how to enable monitoring for windows arc machine.
Launch Azure Arc service, select server from left side pane. Open the connected server. From the left-pane under the Monitoring section, select Insights and then Enable. You have two options, either select Azure monitor agent or log analytics agent.
Virtual machine Insights now supports data collection using the Azure Monitor agent but it is currently in preview mode.
Select log analytics agent, subscription and workspace. Click on configuration to start the process. When the process is complete, a message displays that the machine has been onboarded and that insight has been successfully deployed. Under insights, you can see performance of arc enable VM. You can also see dependency map below.
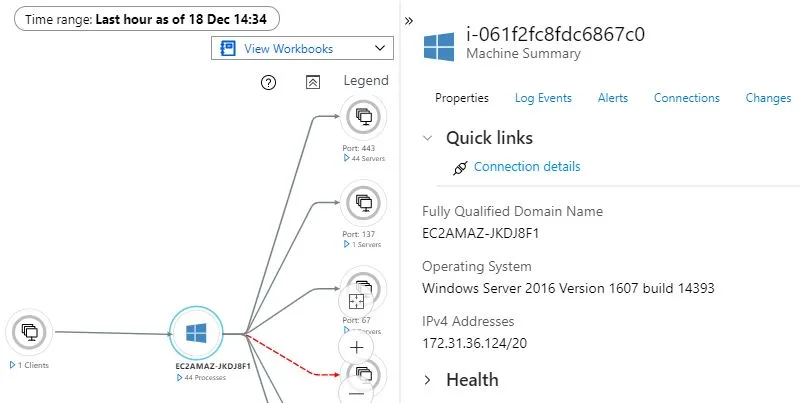
Let’s Takes quick of look of agent services you will find inside Arc Enabled servers.
- The Hybrid Instance Metadata service (HIMDS) manages the connection to Azure.
- Guest Configuration Arc Service monitors desired state of the machine. Audits and enforces Azure guest configuration policies.
- Guest Configuration Extension Service installs the requested extensions. Responsible for Installs, updates, and manages extensions on the machine.
When you enable Azure Arc-enabled servers for multiple windows or Linux machines. You can choose options like by service principle, Configuration manager script, group policy, ansible playbook and Automation update management.
If You need SIEM service for arc enabled servers to collect security related event, you can onboard Microsoft sentinel
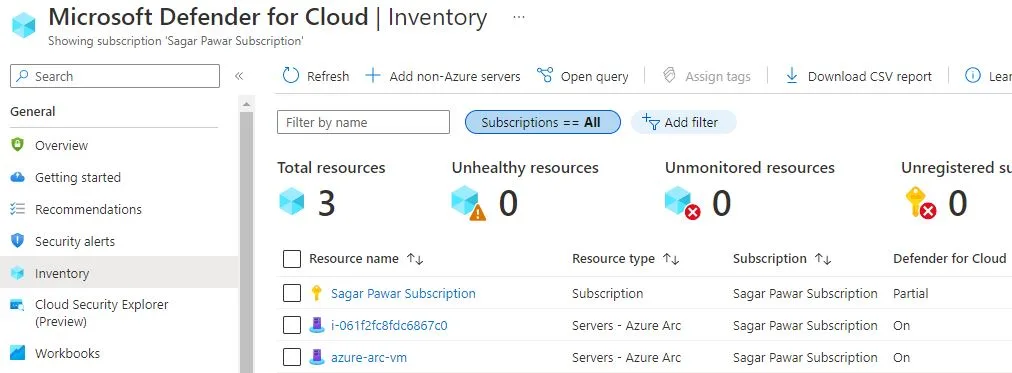
When you’ve installed the Log Analytics agent on it – appears in Microsoft Defender for Cloud dashboard with recommendations like your other Azure resources as shown below.
Using Windows Admin Center in the Azure portal you can manage the Windows Server operating system of your Arc-enabled servers. You can securely manage hybrid machines from anywhere–without needing a VPN, public IP address, or other inbound connectivity to your machine.
You can access arc enabled servers from Azure Portal via SSH Access. It is common for windows and Linux machine.
Points to be noted :
- If the Azure region your machine connects to is affected by an outage, the connected machine is not affected, but management operations using Azure may be halted.
- Azure Arc-enabled servers has a limit for the number of instances that can be created in each resource group
- Azure Arc-enabled servers doesn’t store/process customer data outside the region the customer deploys the service instance in.
- Agent services installed in arc enabled servers, are designed to use up to 5% CPU each. Based on your requirement, you may install other services for monitoring purpose, CPU utilization of that services may vary.
- Other than script, you can connect to non-azure machine from windows admin center , PowerShell or PowerShell DSC
- You can not manage life cycle of servers through Azure Arc.
What’s Next :
In coming months, you will see more news features. Few are in preview and beta modes. With this service, Multi-clouds management is on demand.
I will release more articles on it making my hands dirty . Thanks for reading. Stay in touch with #Multicloudsagar to keep updated. Keep learning and growing.
Leave a Reply